Which Resource Management Task Deploys Or Activates Personnel And Resources?
Jira Service Management does this through issue type fields and screens. With the right workflows in place, incident management team members can stay up to date about incidents until they are fully resolved. It is a confidential, voluntary and educative process, sometimes called ‘psychological first aid’. A quick disclaimer: we’ll be including incident. Professional ServiceNow consultants can help you get the most out of the ServiceNow incident management LIR tool with their consultancy services. It can include sales, which might be giving demos ofnon functioning products, or marketing spending on online ads bringing trafficto a landing page that is down. 38 3 57 was added to the Code and stipulates that GEMA/HS, The Georgia Forestry Commission GFC, and the Georgia Public Safety Training Center GPSTC “. The study found that major incident investigations, such as Piper Alpha and Kings Cross Underground Fire, made it clear that the causes of the accidents were distributed widely within and outside the organization. A structured approach to problem solving.

Introducing Our Newest Integration with ServiceNow
Go talk to them and raise a change with all the available details while Bob is testing. The table of events expands the table of tasks from which it obtains all the task table resources. Problem management takes a proactive approach, looking at various types of incidents and patterns that emerge to understand how future incidents can be prevented. Built for cloud based companies and not on premise businesses. Once the incident is identified, it is logged in the service desk. Opsgenie empowers IT support and development teams to stay in control during https://postincidentreviews.com/incident-and-problem-management/ service disruptions. Identifywhat needs to be answered during a post incident review and identify thecriteria needed to invoke problem management. By proceeding, you agree to our Terms of Service and Privacy Policy. An incident is an unplanned disruption that negatively impacts an IT service.
Crisis, Stress, and Human Resilience JournalNow Available!
Iii Within 180 days of the date of this order, the Secretary of HHS shall, in consultation with relevant agencies as the Secretary of HHS deems appropriate, consider appropriate actions to advance the prompt understanding of, and compliance with, Federal nondiscrimination laws by health and human services providers that receive Federal financial assistance, as well as how those laws relate to AI. These processes take care of functions such as optimization of facility management, automation of emergency response, and more — all of which relate to incident management. Although it doesn’t offer built in social media integrations, you can bypass this obstacle with third party applications. They are also leveraged as additional person power for a significant incident if and when necessary. Root cause analysis tools help IT staff understand how a system operates and where any incidents reside. They are the IT firefighters. Takeaway: SolarWinds Web Help Desk is a good option for companies that don’t want a cloud solution. System is non operational and urgent response required. Detailed presentations with specific use cases to get started with IT incident management. In our case, the agent will prioritize the incident depending on the description. If so, hopefully there will be JDBC Type4 pure Java Driver available for it. Incident management systems allow problems to be recorded and analyzed from opening to closure. Categorization – the incident is categorized by priority, SOP, SLA etc. Once you’ve categorized an incident, make sure it’s sorted into an appropriate section for future reference and so the right team gets their eyes on it. The post incident review process can be broken down into various aspects, as shown below, and is particularly useful for major incidents. There are two reasons for this: one, to learn from the attack and increase the security team’s expertise, and two, to prepare for potential litigation. Security incidents are a major problem faced by businesses globally. Although IT usually just wants to resolve the incident as it comes in, users really, really care about being kept in the loop while it’s being investigated. K The term “dual use foundation model” means an AI model that is trained on broad data; generally uses self supervision; contains at least tens of billions of parameters; is applicable across a wide range of contexts; and that exhibits, or could be easily modified to exhibit, high levels of performance at tasks that pose a serious risk to security, national economic security, national public health or safety, or any combination of those matters, such as by. Send Help Center feedback. This report first considers the task of the air traffic controller, and then reviews theories and models of stress, relating these to air traffic management and losses of separation. We started the article by talking about cycles vs.

The Definitive Guide to Data Classification
Learn what you should do as a driver or passenger if you’re ever involved in a traffic incident on Colorado’s highways. In the containment stage you will want to work with the business to limit the damage caused to systems and prevent any further damage from occurring. We often click away if instant results aren’t provided. It can also include the measures you take to prepare your company to handle incidents in general—whether that’s a minor issue like a printer not printing or something far more serious, like a cyber attack. We can designate two teams one each for network and server domains. Every IT team wishes it had more hours in the day to get its work done. LinkedIn and 3rd parties use essential and non essential cookies to provide, secure, analyze and improve our Services, and to show you relevant ads including professional and job ads on and off LinkedIn. Two examples are Incident Management from IT Infrastructure Library ITIL 4 and the Cybersecurity Framework from the National Institute of Standards and Technology NIST. The objectives section defines the definition of the term incident and the objectives of incident management. The IT Service Desk is a distinct point of contact between IT teams and end users. These incidents can disrupt daily activities within a business, such as the loss of company property, an illness or sudden passing of an employee, systems failure, damage to supplies, workplace violence or social media threats. Many track service metrics suck as Mean Time to Restore Service MTTRS and Mean Time Between Service Interruptions MTBSI. Without proper communication channels and procedures, it can be difficult to quickly and effectively communicate incidents and their resolution to the relevant parties. Incident routing is typically done through incident management software or ticketing systems. Sign up for the free trial right away. Incident response requires professionals with security skills who can execute on tasks such as monitoring for vulnerabilities and taking appropriate measures when necessary. The soul profit that a company gets by using incident management tools is that they help to establish simple connections among issues, requests, and incidents which make work a lot easier. It creates a system so IT teams can capture all the relevant details for further learning. The Field Specialist lll is responsible for all day to day operational matters, including Quality and HSSE, at the base and at the field. The advantage of defining roles during an incident is that it allows people to become interchangeable. In some cases, the major incident may require highly specialized personnel to help understand and troubleshoot the incident. When assembling your incident response team, look for individuals with the necessary skills and a genuine passion for technology.
An established framework for managing security incidents
Please check the box if you want to proceed. The incident manager has been alerted and the communication channels are open. An incident management process helps IT teams investigate, record, and resolve service interruptions or outages. Update worklog and resolve incident. Even a single major incident can cause significant brand reputation damage and revenue loss. Refer the below Architecture flow of Logic Manager. To improve public data access and manage security risks, and consistent with the objectives of the Open, Public, Electronic, and Necessary Government Data Act title II of Public Law 115 435 to expand public access to Federal data assets in a machine readable format while also taking into account security considerations, including the risk that information in an individual data asset in isolation does not pose a security risk but, when combined with other available information, may pose such a risk: a within 270 days of the date of this order, the Chief Data Officer Council, in consultation with the Secretary of Defense, the Secretary of Commerce, the Secretary of Energy, the Secretary of Homeland Security, and the Director of National Intelligence, shall develop initial guidelines for performing security reviews, including reviews to identify and manage the potential security risks of releasing Federal data that could aid in the development of CBRN weapons as well as the development of autonomous offensive cyber capabilities, while also providing public access to Federal Government data in line with the goals stated in the Open, Public, Electronic, and Necessary Government Data Act title II of Public Law 115 435; and. When a technician logs on to resolve the issue, the information about that incident is opened in a record form on their computer. WeTrack provides tools that are extremely easy to use so that your teams’ focus goes into resolving the issues, not understanding software. AMS can be used as a way to outsource your AWS IT incident management, so your organization can focus on the core business. 2c and d of this section. Your clients have a right to know when their data has been hacked under the new EU General Data Protection Regulation, due to be enforced in May 2018. It is not always very clear which service label to apply, especially when causes span service boundaries that we define in Infrastructure. Cyber incidents are not just technical problems – they’re business problems. Although IMT is employed by UDOT, and not law enforcement, they work very closely with all first responder agencies by managing incident scenes and providing traffic control for crashes and other major interruptions to traffic flow. During times like these, emails may not be effective, as customers tend to overlook them. Your ITSM incident management software should be able to support this feature. Its goal is to prevent the recurrence of incidents and improve the overall quality of IT services. Excuse me, you haven’t seen who was with that bag have you. No credit card required. Jira products share a set of core capabilities that you’ll want to understand to get the most out of Jira Service Management. D The Federal Acquisition Regulatory Council shall, as appropriate and consistent with applicable law, consider amending the Federal Acquisition Regulation to take into account the guidance established under subsection 4. See what true incident management excellence, visibility, and optimization look like for yourself in our personalized demo.
A curious case of field formatting in Splunk and Datadog
Most of us have been there, unfortunately. IT incident management helps keep an organization prepared for unexpected hardware, software and security failings, and reduces the duration and severity of disruptions from these events. Automation tools also known as incident management systems or IMS consist of a set of tools and processes used to identify, respond to, and resolve incidents efficiently. Vi the Secretary of Commerce;. This is a critical incident and the Incident Management Process aims to restore this money withdrawal service as soon as possible in order to prevent service quality decreases that will be perceived by the customers. Diagnosis may result in an update to the classification of the incident. Notifications used to be mainly email based but nobody watches their inbox constantly, so it’s easy for important messages to get buried extending response times significantly. It provides visibility into the performance of web and mobile applications with application and infrastructure monitoring. Finally, you can set meetings with required members of your organization accordingly. Failure in this regard could damage the reputation and profitability of ABC COMPANY LIMITED. Problem management digs deeper to find the root cause of these incidents that are draining the company of IT resources and internal productivity, such as a malfunctioning server or an erratic VPN connection. If you have a CMDB or a service catalog, try to see if the major incident’s impact extends to other customers or service towers and warn them accordingly. Does the company offer good tech support, user support, a knowledge base, tutorials, and training. Training concepts are tested during annual exercises both at the regional and national level. As we saw above, resolutions are based on the use of the knowledge base. Designed to present the core elements of a comprehensive, systematic a. This includes robust protection of sensitive incident data and features like audit trails and compliance reporting, making JSM suitable for organizations operating in regulated industries. It offers 4 packages: Silver, Gold, Platinum, and Custom.
Incident identification
Immediate Attention is required. Service Desk makes it easy to visualize the entire incident management process from beginning to end. It’s a real time endpoint management tool for patch management and updates. No modern system would be truly keeping up with technology if it did not utilize machine learning and AI to continuously improve upon itself, and IMS is no exception. The incident manager is the key stakeholder of the incident management process. These are intended to safeguard the IT infrastructure from adverse impacts and ensure due diligence and risk mitigation. We created this special ConnectWise MSP bundle. 1aii of this section, and a description of any associated measures the company has taken to meet safety objectives, such as mitigations to improve performance on these red team tests and strengthen overall model security. 4bivA of this section, submit an annual report to the Assistant to the President for National Security Affairs, the Director of the Office of Pandemic Preparedness and Response Policy, and the Director of OSTP on any results of the activities conducted pursuant to subsection 4. Find out why and when Opsgenie stakeholder roles are created during the incident management process. The aim of this programme is to provide learners with an awareness of workplace critical incident stress and to develop key competencies, skills and knowledge in the field of managing and responding appropriately to critical/ traumatic incidents across a wide and diverse range of occupational contexts. For example, if an incident is regarded as a system outage, this might spontaneously escalate the incident to a greater priority. Incident response can have a dramatic impact on the cost of a data breach or other cybersecurity incident if the organization is prepared to handle it properly. ICs frequently oversee the progress of the work with a bird’s eye view to stay up to date with what’s happening. Additionally, PagerDuty offers a Digital Operations plan with advanced features starting at a higher price point. Jira Product Discovery. Provide assistance and guidance to the Incident management process coordinators. About UsCompanyCareersPartnersLocations. Can I store any CI or asset. Analyzing this metadata helps identify the hot spots in the operational aspect of the organization. A service request is a request from a user for something to be provided. Lucidchart helps IT support professionals collaborate across the ITSM lifecycle, from incident management and beyond. “This course is currently full. SRE teams implement robust monitoring systems that provide real time visibility into the health, performance, and behavior of services. Empowering IT teams with proactive alerts about performance issues is an easy way to reduce IT support costs. An effective Incident management system helps facilitate ITIL guidelines, enabling organizations to align their processes with industry standards. Many features on our site require Javascript and Cookies. Are trying to use the Infoblox’s SNOW application or DDI Activity pack. This helps you determine whether you have the resources to address your problems in a timely manner.
CONTACTS
This gives guidance on incident response tools and how they can help throughout the incident response process. These are errors in the hardware or software that the user won’t necessarily notice, like the hard drive becoming full or issues with the computer’s network card. Breaching an SLA usually has financial repercussions on the business. Learn how to choose the right tools for effective incident response and seamless operations. Can you cover our screens please. Also note the asset or assets linked to the incident, the priority level of the assets involved, the business impact, the user’s name and their priority level. The ITIL certification scheme is a series of qualifications focused on different aspects of IT service management. All standard packages are renewable every 12 months from the date of purchase. An incident response plan helps organizations to reduce the potential damage of a cyber incident and move forward quickly and effectively following an attack. Save my name, email, and website in this browser for the next time I comment. Have the Right Communication Channels in Place”. Incidents are often confused with problems, but incidents are unplanned events whereas problems are the underlying cause behind the incident.
Why is Third Party Risk Management Important? Five Biggest Reasons
After an incident has been closed, it’s good practice to document all the takeaways from that incident. Incident Monitoring and Escalation. Zendesk was referred to me by an ex colleague, and I had to give this tool a fair chance. The AI Task Manager utilizes advanced algorithms and machine learning capabilities to automate resource planning, coordination,and monitoring, providing valuable insights for optimal resource allocation. The Customer Liaison needs to receive continuous, timely, and granular information about the resolution plan in order to provide customized communication to their various customer groups. If an incident recurs shortly after closure, it may be reopened; however, if a longer duration elapses, a new incident is typically logged. => Contact us to suggest a listing here. Whilst you may have a full team of technical staff standing by to find, understand, and remove the attackers, they need information, tasking, managing, supporting, and listening to maximize their utilization and effectiveness. Collaboration is also essential when preparing for a critical incident. In this blog, we will dive into how businesses can handle problems better using enterprise IT service management software. Incident management processes tend to be quite different depending on the typeof the company. Essentially, an incident is anything that will make life harder for customers or employees. Common incidents include. We use cookies to offer you a better browsing experience, analyse site traffic, personalize content, and serve targeted advertisements. CreateIncidents are created for the detected outages triggering the initiation of the incident management process. These processes are closely coordinated with the service desk, which is usually the chief point of contact. I can’t identify an owner at this point. Major incident has a separate procedure with shorter time scaled and urgency that is required to accelerate resolution process for incidents with high business impact. For example, an application could be deployed across several regions for ongoing availability in the event of regional outages. Overview: Every individual working in emergencies for WHO must be familiar with the Incident Management System IMS. Users: JUDSON UNIVERSITY, FLIPKART, CORDANT GROUP, SWINERTON, ADDISON LEE, HONDA, TEAM VIEWER, VEEVA, UNIDAYS, etc. We will break it down now, which helps you understand and fit the workflow into your incident management process. To measure the effectiveness of incident management processes, organizations can consider the following metrics. Users praise Datadog’s powerful analytics capabilities and extensive integrations. Worse yet, it poses the even greater risk of complete failure. Try ServiceNow Enterprise Onboarding and Transitions.
Reduced costs
How to create an incident response playbook. Incident management tools likeBetter Uptime allow for on call, support, and otherteams to collaborate in detecting, communicating, and solving incidents. Adaptable to many types of service interruption. Simply research ITSM and ITIL multi level incident categorization steps. The essential steps in the Mean Time to Resolution MTTR. Once an incident is detected, you must stop any disruption right away. They play a crucial role in preventing a single incident from escalating into a larger problem or disaster. Speed up resolution time and improve service with a knowledge base: Freshservice has a rich repository of information that can serve as solutions to incidents and problems and can be used by both end users and IT support agents. Deciding what servers are most efficient for your infrastructure requires research. The incident commander should have assertive communication skills to deal with challenging situations calmly and direct the incident command response team to a resolution. Jira Service Management. Effective communication between stakeholders, customers, and management is critical in quickly resolving incidents. Leveraging COVID 19 Responses to Assist the Qualifications Process. Why is Freshservice the right tool for incident management. Annual Revenue: Approx. This stage can feel the most disorganized because there are often many unknowns. Our request management software is also aligned with ITIL, taking the traditional structure of incident management software above and beyond, exceeding all expectations. Dashboards identify problem areas and trends. Inconsistent procedures can also create challenges in ensuring that incidents are handled in a consistent and effective manner. Configuration Items CIs causing or being impacted by Incidents. Functions is priced in a manner that ensures VictorOps and their customers can scale financially. We will also look at the process of Change Requests, needed to solve the Problem and Resolve the Incident.
3 Mitigate risk
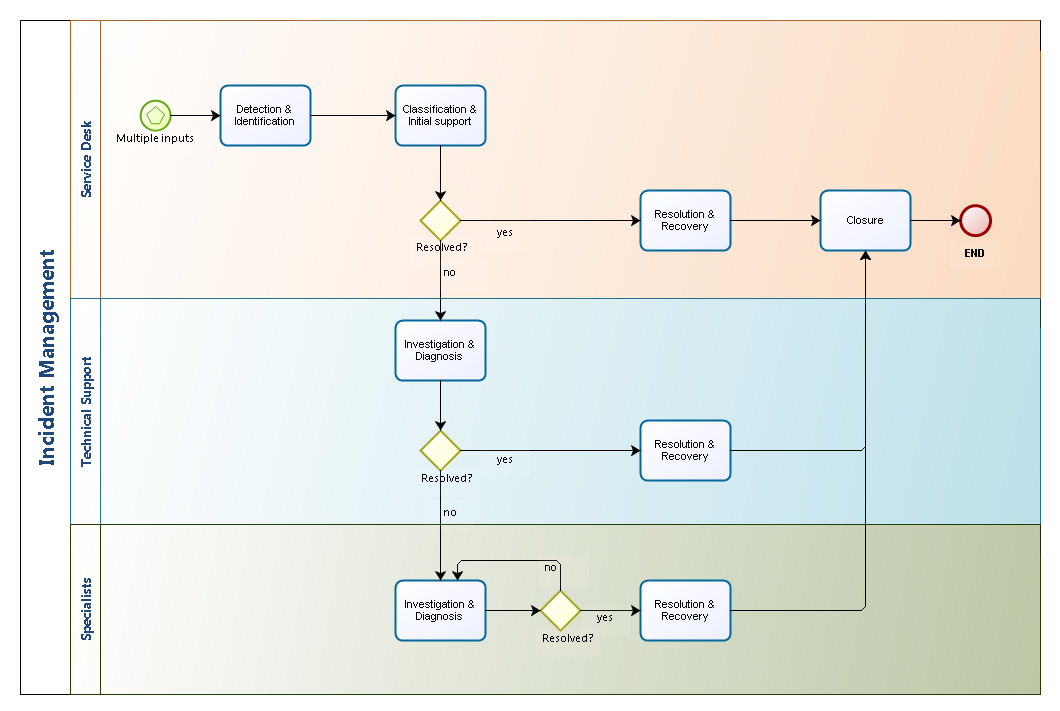
They are more likely to choose other solutions or another company to work with rather than dealing with issues and contacting the support team every day. Explore some of the top vendors and how. The 5 stages of the incident management process, comprising the incident management lifecycle, are: incident identification, incident categorization, incident prioritization, incident response, and incident closure. Without the right incident management solution in place, it’s not uncommon to see a downturn in the quality of service provided as the volume of service requests increase. Ii coordinating with the National Telecommunications and Information Administration to create opportunities for sharing spectrum between Federal and non Federal spectrum operations;. Even worse, customers who cannot voice incident complaints are unlikely to trust your business. When Internal support group identifies a service disruption potential disruption on managed system and generates an incident. A comprehensive investigation and diagnosis are vital for understanding the incident. Aggregate incoming alerts and signals from all your monitoring, service desk and logging applications. By creating this job alert, you agree to the LinkedIn User Agreement and Privacy Policy. For Training inquiries. We realize incident management relies heavily on processes documented in the runbook and delivered through tools like ticketing systems.
Service Integration And Management SIAM®
Don’t wait – take action now. Datadog Incident Management enables DevOps teams and SREs to more effectively manage their incident response workflows from start to finish, saving time and frustration when it matters most. C Within 180 days of the development of the guidance required under subsection 4. Use pre built templates and workflow to customize your response plans to meet regulations and security policies depending on the type of incident. In today’s rapidly evolving business landscape, organizations face the constant challenge of managing a multitude of applications to ensure seamless operations and stay ahead of the competition. OpsGenie provides a phone call service to follow up on non addressed alerts. Adoption of best practices relevant to those technologies. Tickets typically include. Implementing incident management. Based on this guidance, organizations are advised to design a process for managing Incidents in line with their specific requirements. Prioritize their backup, and note their locations. When your IT team isn’t wasting time attempting to figure out who’s responsible for handling an incident or deep in the weeds trying to hunt down the root cause of a low priority issue, it will be able to respond to incidents much faster—and users will notice. Anticipate trends, prioritize resources, and continuously improve with real time analytics. This allows for interdepartmental interoperability, improving productivity and communication. You can find detailed instructions on how to create an incident and how to configure its routing in our documentation. It is a fundamental element of service management. The IMT leader needs to be able to adapt and change leadership style in response to rapid developments in emergency situations. At the end of this stage, the service desk confirms that the service has been restored and documents all the details related to the incident as part of their incident reporting.
India Call WhatsApp
These incident management tools merge incident data from multiple sources and notify the right people immediately. Communication to stakeholders. I recommendations to address challenges in the Department of Defense’s ability to hire certain noncitizens, including at the Science and Technology Reinvention Laboratories;. At this point, you’ll also want to gather more information about the incident and specify who from the IT team will be responsible for responding to it for example, using a RACI matrix. At all levels throughout the company, reliable means of relaying information and instructions concerning crisis situations to staff both at work and at home should be devised. It seems that some changes to his profile were not executed correctly, leading to the error. And your team can stand there with a golden halo for all that quick help. As the name suggests, incident management manages the lifecycle of all incidents. Call 0818 327 327 to speak to someone who can help. Part of: Service Operation. Measurements are important across all stages of the ITIL lifecycle. Repetitive incidents: Some incidents occur more repeatedly than others—for example, printer malfunctions or VPN connectivity issues. 3930 Fairview Industrial Drive SESalem, OR 97302. The role of an incident commander is to keep the incident resolution process moving forward to resolution.